Fix admin consent for SP token retrieval flows in SPFx
This post is over a year old, some of this information may be out of date.
There have been a couple of changes in SharePoint recently related to retrieving access tokens for your SharePoint Framework solutions. One of the changes is that MSAL V3 now uses the /_api/Microsoft.SharePoint.Internal.ClientSideComponent.Token.AcquireOBOToken API to retrieve the access token. Typically, this API was only used when loading your solution from Microsoft Teams, but it will now also be used when loading your solution from SharePoint.
Due to this change, one customer started to experience issues with their SPFx solution. The solution used the @pnp/graph library to retrieve the access token and call the Microsoft Graph API. They noticed the solution was no longer working and were redirected to the /_forms/spfxsinglesignon.aspx page.
The /_forms/spfxsinglesignon.aspx page is used to overcome an issue with third-party cookies or when something goes wrong with token retrieval.
The issue
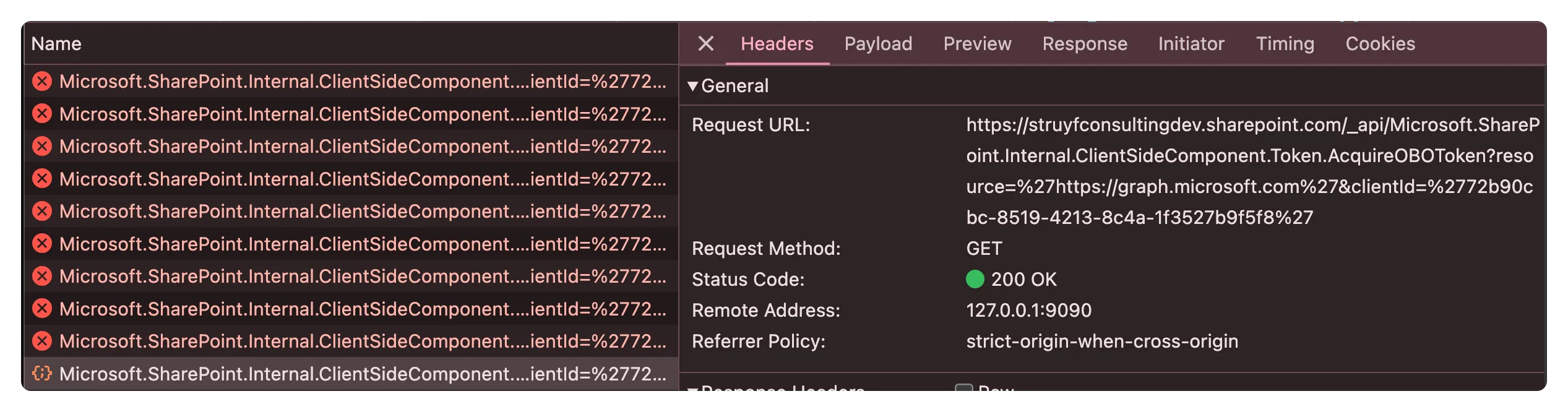
When looking into the issue, I saw failing calls to /_api/Microsoft.SharePoint.Internal.ClientSideComponent.Token.AcquireOBOToken?resource="https://graph.microsoft.com"&clientId="72b90cbc-8519-4213-8c4a-1f3527b9f5f8".
The error message that was returned was the following:
{ "odata.error": { "code": "10001", "message": { "lang": "en-US", "value": "AADSTS65001: The user or administrator has not consented to use the application with ID '00000003-0000-0ff1-ce00-000000000000' named 'Office 365 SharePoint Online'. Send an interactive authorization request for this user and resource. Trace ID: 322f4528-fb10-4407-89e4-9de76da38900 Correlation ID: 827721a1-4047-8000-9395-cd41d1d50a48 Timestamp: 2024-04-22 10:12:52Z" } }}What was weird is that the error message mentioned the 00000003-0000-0ff1-ce00-000000000000 or Office 365 SharePoint Online application ID, as this trust should be automatically set.
When the page got redirected to the /_forms/spfxsinglesignon.aspx page, the following message was returned in the query string:
AADSTS650057 Invalid resource. The client has requested access to a resource that is not listed in the requested permissions in the client's application registration. Client app ID 08e18876-6177-487e-b8b5-cf950c1e598c (SharePoint Online Web Client Extensibility). Resource value from request 72b90cbc-8519-4213-8c4a-1f3527b9f5f8.The solution
The issue was that the SharePoint Online Client Extensibility Web Application Principal Entra app was missing the Authorized client applications for the SharePoint Online Web Client Extensibility app and Office 365 SharePoint Online.
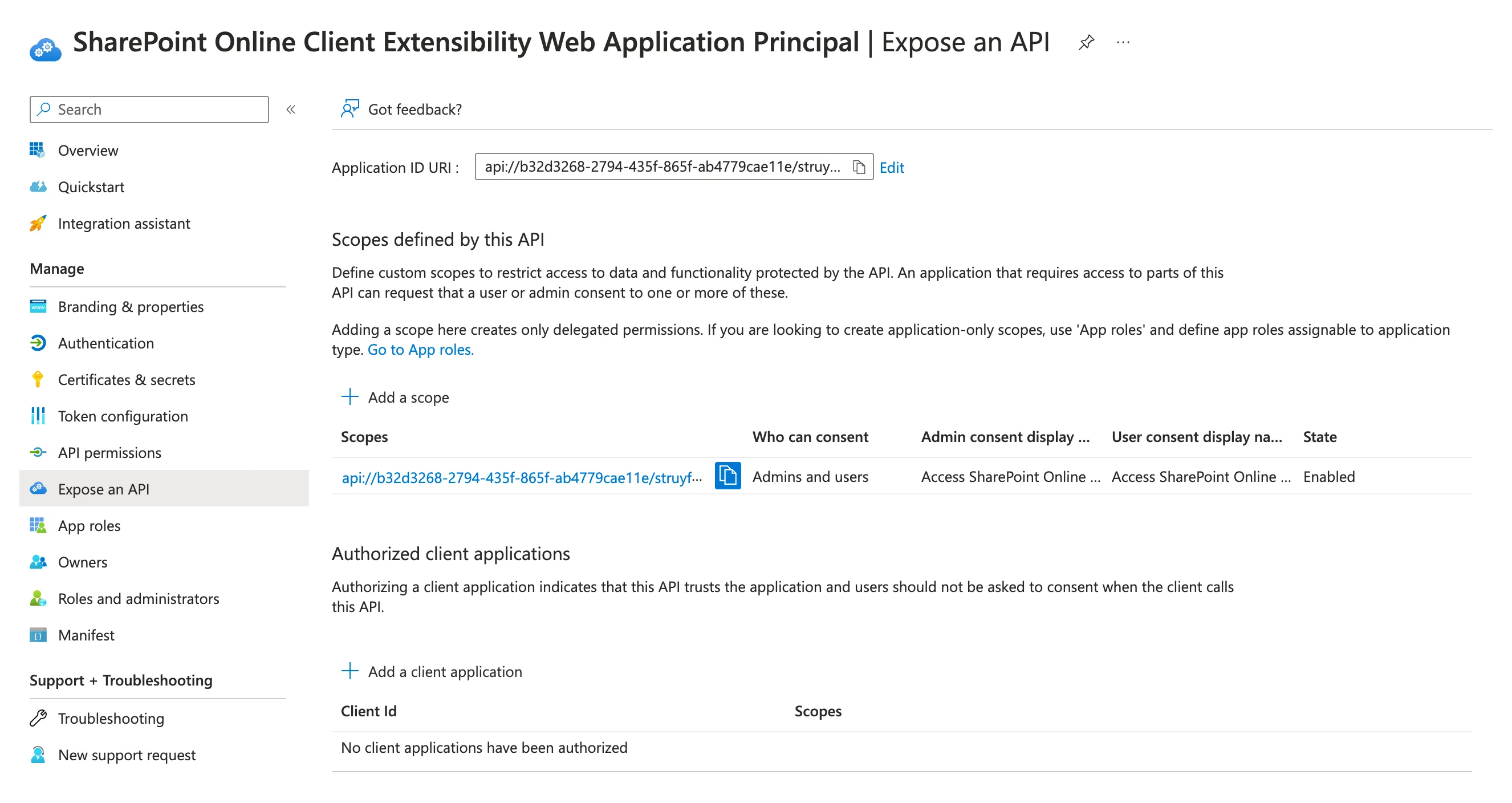
To fix this issue, you need to add the following client IDs to the Authorized client applications of the SharePoint Online Client Extensibility Web Application Principal app:
08e18876-6177-487e-b8b5-cf950c1e598c(SharePoint Online Web Client Extensibility)00000003-0000-0ff1-ce00-000000000000(Office 365 SharePoint Online)1fec8e78-bce4-4aaf-ab1b-5451cc387264(Microsoft Teams)5e3ce6c0-2b1f-4285-8d4b-75ee78787346(Microsoft Teams Web Client)
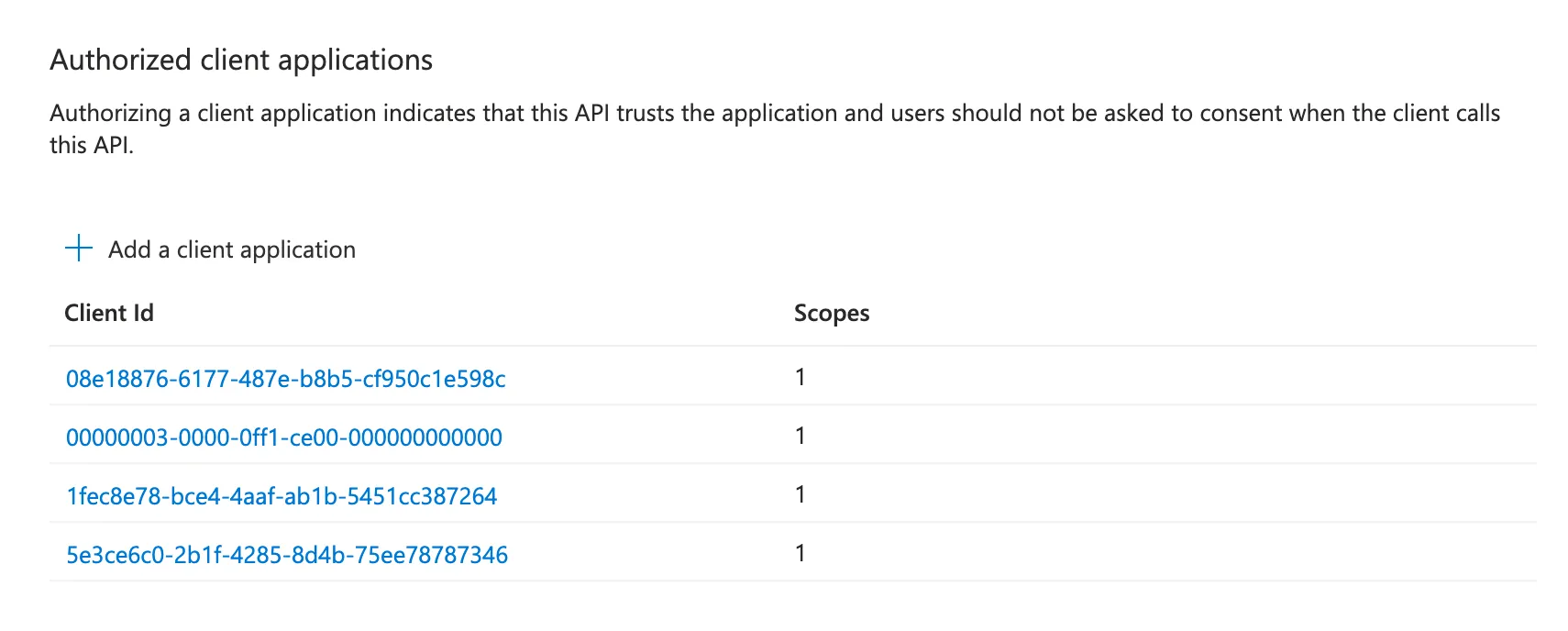
I do not know why those apps were missing from the configuration. They should normally be automatically added when accessing the SharePoint admin API access page. The solution started to work again once the first two client IDs were added.
Related articles
Why it is important to keep the version in sync when using the library component in SharePoint Framework
Retrieving the image its focal point of a SharePoint Modern page
Approve a multitenant permission scope for a SPFx solution
Troubleshooting SharePoint Permission Approval: Learn how to create a Service Principal and define the correct resource for successful permission scope approval
Report issues or make changes on GitHub
Found a typo or issue in this article? Visit the GitHub repository to make changes or submit a bug report.
Comments
Let's build together
Manage content in VS Code
Present from VS Code
Engage with your audience throughout the event lifecycle
